Implementing Cybersecurity Measures for PLC Systems
In an era where industrial automation has become the backbone of manufacturing and critical infrastructure operations, the security of Programmable Logic Controllers (PLC) can no longer be an afterthought. PLC systems, integral to the automated processes, have become targets for sophisticated cyber threats, endangering not just the operational continuity but also the safety of personnel and the public. This blog post delves into the multi-layered strategies needed to fortify PLC systems against the looming cyber dangers. From understanding the essentiality of PLC security to developing a robust incident response plan, we will guide you through a comprehensive approach to safeguard your industrial control systems. Join us as we explore how to identify vulnerabilities, select appropriate cybersecurity measures, and foster a culture of awareness among employees to shield your PLCs and ensure the smooth sailing of your operation’s digital integrity.
Understanding the Importance of PLC Security
Programmable Logic Controllers (PLC) are pivotal in the realm of industrial automation, orchestrating the core operations of machinery and production processes. The security of PLCs entails safeguarding these critical components from unauthorized access or cyber threats that may disrupt industrial operations, potentially resulting in catastrophic outcomes for both safety and financial stability. Appreciating the significance of PLC security is essential, for a breach in these systems could manipulate the operational parameters, leading not only to substantial revenue loss but also to endangering human lives and the environment.
Enshrouded by the realm of industrial control systems (ICS), PLC security transcends the conventional cybersecurity protocols due to the specific nuances of operational technology (OT) environments. It demands an insightful understanding of industrial network architecture, and the commitment to operational continuity, while mitigating vulnerabilities that could be exploited through cyberphysical means. The mere notion of PLC security being compromised is enough to elevate the concerns surrounding the reliability and safety of complex industrial ecosystems.
Emphasizing the importance of PLC security advocates for diligent efforts in devising and enacting comprehensive security frameworks which encompass not only technical controls like authentication and encryption but also resilient policies and practices tailored for the unique landscape of OT. In light of the ever-evolving cyber threat landscape, the resilience of PLC systems against these threats is a compelling argument for ongoing investment in cybersecurity measures, indicative of an organization’s commitment to safeguarding its operational integrity against the increasingly sophisticated arsenal of cyber adversaries.
Understanding the magnitude of PLC security illuminates the stark reality that a proactive cybersecurity posture is far more than an IT mandate; it is an integral component of modern industrial strategic planning. A breach in PLC security implicates a domino effect that may resonate far beyond the immediate operational disruptions—it gestures towards reputational damage, regulatory scrutiny, and long-term economic repercussions. Thus, the quest for robust PLC security is undeniably crucial for maintaining the delicate balance of productivity, safety, and cybersecurity in the industrial domain.
Identifying Vulnerabilities in PLC Systems
Understanding the intricacies of network security is paramount in the industrial sector, particularly when it comes to safeguarding Programmable Logic Controllers (PLCs). By meticulously identifying the vulnerabilities that may exist within PLC systems, companies can effectively mitigate potential risks and fortify their defenses against unauthorized intrusions and cyber-attacks. Comprehensive vulnerability assessments must be routinely conducted to scrutinize every possible angle, ensuring the security of critical infrastructure that relies heavily on these systems.
Within the complex web of industrial control systems, PLCs can be the linchpin for operational continuity; therefore, recognizing the importance of securing these devices cannot be overstated. Often, vulnerabilities stem from outdated firmware, insufficient access controls, or the use of default credentials, which provide fertile ground for cyber threat actors to exploit the system. Organizations must employ vigilant security practices and leverage specialized tools to systematically scan for weaknesses, assessing not only hardware but also the software layers that interact with the controllers.
Another significant aspect to consider is the network architecture that PLCs are woven into. Vulnerabilities can often be found in the interstices of communication protocols and third-party integrations, which might lack stringent security measures. Employing a thorough, methodical approach for security review allows for the detection and remediation of inconsistencies and security gaps that could potentially allow cybercriminals to gain control over critical systems. The deep dive into identifying vulnerabilities, therefore, demands both technical acuity and an overarching strategy that aligns with the organizations’ risk management framework.
Finally, in an era where cybersecurity threats are ever-evolving, the endeavor to shield PLC systems from vulnerabilities is a perpetual task that requires constant vigilance and adaptation. Integrating a robust review cycle, inclusive of penetration testing and risk assessments by seasoned professionals, is essential to stay ahead of the tactics employed by adversaries. Meticulous attention to the evolving threat landscape ensures that vulnerabilities in PLC systems are not only identified but also effectively addressed, reinforcing the bastion of security that these indispensable systems demand.
Selecting the Right Cybersecurity Measures
In the current digital landscape, the necessity to enforce robust cybersecurity measures cannot be overstated, especially considering the sophistication of cyber threats. To safeguard sensitive data and maintain business continuity, companies must meticulously evaluate and adopt a tailor-made security strategy that aligns with their unique needs. Importantly, this entails not just any measures, but precisely those that holistically cover the organization’s vulnerabilities and adapt to the dynamic nature of cyber risks.
Selecting the right cybersecurity measures demands a comprehensive understanding of the specific threats that an organization faces. This means conducting thorough risk assessments to identify the most probable attack vectors and potential impacts on the organization’s assets. Subsequently, decision-makers should prioritize a multi-layered security approach, considering solutions such as encryption, secure access controls, and behavioral analytics, which collaboratively create a formidable defense against unauthorized access and data breaches.
Moreover, the implementation of the chosen cybersecurity measures should be an ongoing process, rife with regular evaluations to ensure their effectiveness over time. It is crucial for organizations to stay abreast of emerging threats and evolving compliance regulations, thus ensuring their security infrastructure is not only current but forward-thinking. This forward-looking approach involves investing in innovative technologies like artificial intelligence and machine learning that can proactively detect and respond to anomalies before they escalate into full-blown security incidents.
Ultimately, the goal in selecting the right cybersecurity measures is to establish a resilient security posture that not only protects against current threats but is also scalable and agile enough to respond to the unforeseeable challenges of tomorrow. By cultivating a culture of security awareness and adopting an integrated set of defenses, organizations can effectively shield their operations from the costly and reputation-damaging effects of cyberattacks.
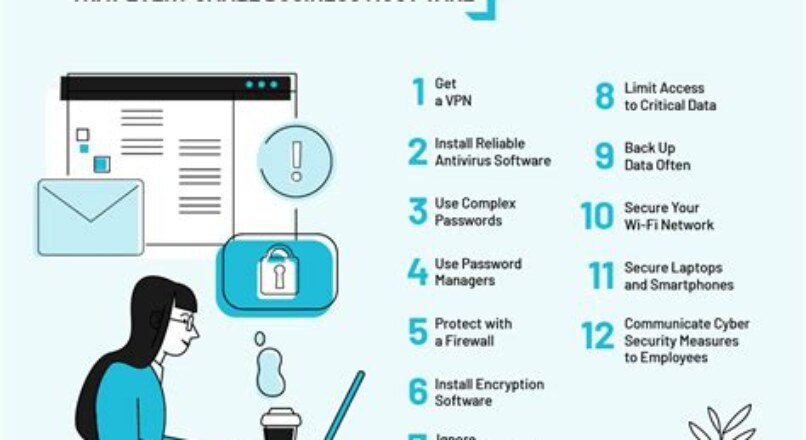
Implementing Strong Password Policies
In the realm of cybersecurity, the implementation of strong password policies is paramount to securing sensitive data and protecting against unauthorized access which, if undermined, can lead to catastrophic breaches and irreparable damage to an organization’s credibility and operations. Enhancing password security is not only a proactive step towards safeguarding digital assets but simultaneously a formidable deterrent to the relentless attempts of cyber adversaries. Crafting intricate passwords that combine a sequence of upper and lowercase letters, numerical values, and special characters, significantly reduces the susceptibility to brute-force attacks whereby malicious entities employ automated software to decode passwords through exhaustive trial and error.
The exigency for organizations to formulate and enforce robust password guidelines cannot be overstressed, as weak passwords are often likened to flimsy locks on vaults teeming with sensitive information – an invitation to hackers searching for vulnerable targets in the digital landscape. Mandating periodic password changes is a vital component of surmounting the myriad of security challenges. It serves to continually shuffle the digital combinations that guard the virtual gateways to critical systems and data, thereby curtailing the window of opportunity for cybercriminals to exploit any potentially compromised credentials.
Furthermore, the implementation of advanced features such as multi-factor authentication adds an additional layer of security to the password infrastructure, requiring users to provide one or more verification factors beyond the password, thus markedly fortifying the defenses against unauthorized intrusions. Additionally, through the education of staff about the significance of a strong password policy, companies can instill a culture of security-mindedness, effectively turning each employee into a vigilant sentinel, standing guard against the ceaseless surge of cyber threats seeking to penetrate the organization’s digital fortifications.
To ensure that password policies do not become an exercise in futility, regular audits and compliance checks must be instituted to verify adherence to security protocols, while also swiftly identifying and rectifying any deviations. By integrating this systemic approach to create and manage secure passwords, organizations can significantly bolster their cybersecurity posture, transforming their password policies from simple passcodes into robust bulwarks that steadfastly defend against the sophisticated stratagems deployed by contemporary digital marauders.
Applying Regular Software Updates and Patches
In the realm of organizational cybersecurity, the act of applying regular software updates and patches stands as a critical defense mechanism against a myriad of cybersecurity threats. By ensuring that software is kept up-to-date, organizations can close the security loopholes that hackers frequently exploit. Long gone are the days when updates were a mere suggestion; in today’s cyber landscape, they provide essential modifications to the system’s security protocols, which protect against the constantly evolving arsenal of cyber-attacks.
It’s not an exaggeration to state that the absence of timely updates and patches can leave a system perilously vulnerable to attacks, which could otherwise be mitigated by addressing known vulnerabilities. Each software update and patch released is typically a response to identified security gaps or operational bugs that, if left unresolved, create potential entry points for cybercriminals. In essence, by proactively implementing updates and patches, one is not merely enhancing the system but is also constructing an ever-evolving fortification against the incursions of malicious entities.
Moreover, in the vigorous pace of today’s technology landscape, the importance of updates and patches has been magnified, as these not only patch existing vulnerabilities but can also enhance system performance and add new features. It is imperative to understand that this process is not a one-time task but a continuous commitment; it requires diligence, foresight, and proactive scheduling to ensure that all operational software is maintained at its optimal state of defense. As it stands, consistent maintenance through regular software updates is no less vital than any other strategic security measures implemented within an organization’s cyber-defense protocol.
It cannot be overstressed that every organization, regardless of size, should place a significant emphasis on establishing procedures for applying updates and patches as seamlessly as possible. This might include automated systems that ensure the immediate deployment of critical fixes or scheduled downtime that permits the necessary updates without disrupting business operations. Ultimately, staying ahead of cyber threats with a disciplined update and patch strategy is not just about protecting data assets; it’s about safeguarding the integrity of the entire digital infrastructure on which modern businesses operate.
Utilizing Firewalls and Network Segmentation
In today’s cyber realm, the profound significance of network security is an undeniable reality for businesses and organizations across all sectors, especially when considering the implementation of industrial control systems such as Programmable Logic Controllers (PLCs). One of the cornerstone strategies in safeguarding these critical systems involves utilizing firewalls and network segmentation, a method which not only fortifies the network against unauthorized access but also minimizes potential damages should a security breach occur. The strategic placement of firewalls functions as robust barriers, scrutinizing incoming and outgoing network traffic and thereby allowing only legitimate communication to pass through.
Investing in sophisticated firewall technologies can substantially mitigate the risks associated with cyber threats; however, the mere deployment of firewalls is not sufficient—a nuanced understanding of configuring and managing these tools is paramount to ensure that they operate at the apex of their capabilities. When it comes to network segmentation, this practice is akin to compartmentalizing the network, creating separate segments for different parts of the organization’s operations. This ‘divide and conquer’ approach limits the horizontal movement of potential threats within the network, ensuring that a compromise in one segment does not automatically endanger the integrity of others.
The task of securing PLC systems demands that attention be steered towards intricate details of network architecture. Deployment of firewalls and network segmentation must be carried out with meticulous planning—taking into account the particular requirements of the system, data flow, and the operational dependencies. Furthermore, the implementation of these security measures should not hinder the performance or availability of the PLC systems, which are often critical to industrial operations and require real-time data exchange with minimal latency. Therefore, it behooves organizations to perform regular assessments and updates of their firewall rules and network segment policies to align with evolving operational needs and external threat landscapes.
In the grand schema of PLC security, the prowess of a well-implemented network segmentation strategy buttressed by efficacious firewalls can dramatically transform an organization’s defensive posture. Continuous vigilance and proactive management form the bedrock on which the security of PLCs and, by extension, the organization’s operational infrastructure, is founded. By championing these measures, businesses are better equipped to thwart cyber attacks, safeguard critical assets, and maintain the resilience and continuity of their operations amidst an ever-growing and sophisticated array of cyber threats.
Implementing Intrusion Detection Systems (IDS)
Implementing Intrusion Detection Systems (IDS) plays a crucial role in safeguarding information systems from unauthorized access and cyber threats, with the primary function of monitoring network and system activities for malicious actions or policy violations. A well-configured IDS serves as a vigilant watchdog, analysing traffic throughout the network to detect suspicious patterns that may indicate a security breach. By promptly identifying potential threats, organizations can respond swiftly to mitigate risks and protect their critical assets from the ever-evolving landscape of cyber attacks.
The intricate process of selecting and deploying the appropriate IDS solution necessitates a thorough understanding of an organization’s unique network architecture and security requirements. It is imperative to bear in mind that the efficiency of an IDS hinges on continuous updates and maintenance to keep pace with the rapidly advancing tactics employed by cyber adversaries. The deployment of an IDS should be complemented with regular system reviews, updates to signatures or anomaly algorithms, and adjustments to reflect the changing network environment, in order to maintain a robust security posture.
Another vital aspect of implementing an IDS is ensuring the system is finely tuned to strike an optimal balance between its sensitivity and the occurrence of false positives. Too many false positives can consume valuable security resources, resulting in ‘alert fatigue’ and potentially causing genuine threats to slip through unnoticed. Conversely, if the sensitivity is set too low, the IDS may fail to detect actual attacks. Crafting a tailored approach to IDS configuration necessitates input from experienced security professionals who can calibrate the system effectively for your distinct network context.
Moreover, the successful integration of an Intrusion Detection System into an organization’s cybersecurity framework is dependent on interdepartmental collaboration. IT and security teams must work closely with other departments to develop comprehensive security protocols and ensure consistent awareness across the board. Through proactive engagement and training, employees become adept at recognizing signs of security incidents, enabling them to contribute to the overall effectiveness of the IDS and fortifying the organization’s collective defense against cyber threats.
Implementing Intrusion Prevention Systems (IPS)
The implementation of Intrusion Prevention Systems (IPS) has become a cornerstone in the field of network security, acting as a proactive and dynamic defense mechanism against a multitude of cyber threats. By placing a strong emphasis on IPS, organizations can effectively monitor traffic in real time, thereby recognizing and responding to suspicious activities before they can inflict harm. The advanced technology leveraged by IPS solutions enables them to not only detect potential threats but also to take immediate action by blocking or containing said threats, thereby significantly limiting the risk of a successful cyber attack.
One of the fundamental steps in the adoption of an IPS framework is to ensure seamless integration with existing infrastructure, allowing for the holistic protection of the network without causing disruptions to everyday operations. Moreover, on the cutting edge of IPS technology, there lies a breed of solutions that employ next-generation techniques such as machine learning and behavioral analytics, turning them into intelligent systems capable of adapting to the evolving landscape of cyber threats. Through this evolving security posture, organizations can effectively mitigate the risks posed by new and sophisticated attack vectors.
Customization and scalability of the system are also crucial factors in implementing an IPS effectively, providing the flexibility to cater to the growing and changing needs of a business. In this regard, IPS solutions can be configured to recognize and allow legitimate traffic corresponding to the operational profiles of the enterprise, whereas anomalous traffic, indicative of a potential security breach, would be immediately checked and dealt with. This level of detailed traffic analysis and control is imperative in maintaining the integrity and confidentiality of sensitive data.
In conclusion, the value of an IPS in safeguarding an organization’s digital assets cannot be understated. A robust IPS strategy ensures that the network is not only protected against known threats but is also equipped to tackle unknown challenges that may emerge. For businesses that prioritize cybersecurity, implementing an IPS is not just an option but an essential component of an all-encompassing security framework designed to withstand the increasingly sophisticated cyber-attacks of the modern era.
Training Employees on Cybersecurity Best Practices
When it comes to fortifying an organization’s cybersecurity infrastructure, one cannot overlook the pivotal role played by employee training. Educating staff on cybersecurity best practices is fundamental, as human error is often the leading cause of security breaches. Without a comprehensive understanding of potential cyber threats and how to counteract them, employees may inadvertently become the weakest link, exposing sensitive data to significant risks. A robust training program should encompass a wide array of topics, including but not limited to, recognizing phishing attempts, safe handling of confidential information, and the implications of weak password practices.
Furthermore, simulations of cyber-attack scenarios are an effective method for reinforcing theoretical knowledge; such exercises help staff to pragmatically apply their training in realistic contexts. Embedding cybersecurity awareness into the company culture is equally crucial as regular training sessions. This continuous education ensures that employees are not only knowledgeable but also vigilant and proactive in identifying and reporting security threats. These initiatives, when combined, can significantly reduce the incidence of security incidents attributed to human error.
Another significant aspect of training employees on cybersecurity is ensuring that they remain up-to-date with the latest security protocols and emerging threats. The digital threat landscape is constantly evolving, necessitating an agile and continuous learning approach. Providing employees with resources and forums for staying informed about new vulnerabilities and defense mechanisms can foster a sense of collective responsibility and empowerment, which is invaluable for the security posture of any organization.
To sum up, the practice of training employees on cybersecurity best practices is a critical investment in an organization’s overall security strategy. Regular and comprehensive training not only equips the workforce with the necessary tools and knowledge to combat cyber threats but also cultivates a secure-minded workforce. This collective mindfulness is a potent shield against the multiplicity of cyber threats that businesses face in an increasingly digitized world.
Developing an Incident Response Plan
A robust Incident Response Plan is a linchpin of any enterprise’s cybersecurity posture, equipping them with a structured protocol to follow in the heat of a security breach. It stands as a blueprint for tackling the myriad of challenges that arise during a cyber incident, diligently guiding the response team through the complex trenches of digital forensics, communications, and system recovery. By meticulously outlining the roles and responsibilities, escalation procedures, and communication strategies, an Incident Response Plan becomes an indispensable handbook for mitigating the impact of cyber threats.
Developing this plan involves a deep dive into an organization’s unique infrastructure and potential risks, enabling the creation of tailored strategies that encompass the nuanced dimensions of the business’s digital landscape. Successful implementation calls for a collaborative endeavor that bridges the technical acumen of IT experts with the operational insight of executive leadership. These multi-disciplinary efforts cultivate a seamless response mechanism, wherein technical resolutions are expertly synchronized with organizational procedures, ensuring minimal disruption to business continuity.
Furthermore, a dynamic Incident Response Plan extends beyond mere documentation. It requires regular exercises and simulations, which act as trial by fire to not only gauge the readiness of response teams but also to refine their approach in alignment with evolving cybersecurity threats. Such iterative updates and drills are essential, transforming the theoretical framework of the response plan into a living organism that evolves with the organization’s size, sophistication, and the shifting nature of the cyber threat landscape.
Lastly, the essence of an Incident Response Plan is ingrained in the philosophy that ‘prevention is better than cure’, yet it also acknowledges the inevitability of security incidents in today’s hyper-connected age. This pragmatism accentuates the need for having a comprehensive plan that not only facilitates a swift and structured response but also underscores the importance of resilience and the capacity to recover with agility. By doing so, organizations empower themselves to navigate the complexities of cyber adversities with confidence and composure.
Frequently Asked Questions
Why is PLC security crucial for industrial control systems?
PLC security is vital as it protects critical infrastructure and industrial control systems from unauthorized access, manipulation, or sabotage that could lead to downtime, safety hazards, and financial losses. Ensuring the security of PLCs helps maintain the integrity and reliability of these systems.
What are common vulnerabilities found in PLC systems?
Common vulnerabilities in PLC systems may include weak authentication mechanisms, outdated software, lack of encryption, improper network configurations, and insufficient access control measures. These weaknesses can be exploited by attackers to gain control over the systems.
How should companies approach selecting cybersecurity measures for their PLC systems?
Companies should conduct a thorough risk assessment to identify specific threats and vulnerabilities and then select cybersecurity measures that address these issues effectively. They should consider factors like the criticality of the system, the potential impact of breaches, and compliance with industry standards.
What role do strong password policies have in protecting PLC systems?
Strong password policies are the first line of defense. They prevent unauthorized access by ensuring that only individuals with complex, regularly updated passwords can access the PLC systems. Policies should enforce password complexity, change intervals, and account lockout mechanisms.
What is the importance of applying software updates and patches for PLC security?
Regularly applying software updates and patches is critical for correcting security vulnerabilities that could be exploited by attackers. This proactive approach helps protect PLC systems against known threats and reduces the risk of cyber incidents.
How can firewalls and network segmentation enhance the security of PLC environments?
Firewalls and network segmentation are strategic defenses that limit communication between networks and control which traffic is permitted. This compartmentalization helps contain any potential breaches and minimizes the spread of cyber threats within an organization’s network infrastructure.
Why is employee training on cybersecurity best practices important for protecting PLC systems?
Employee training is crucial because human error or lack of awareness can lead to security breaches. By being educated on best practices, employees can recognize potential threats, follow proper protocols, and contribute to the overall security posture of the PLC environment.